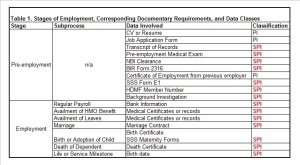
In the previous installment, we outlined the potential entry points where personal information or sensitive personal information (PI and SPI, respectively) as defined by the Data Privacy Act of 2012 may enter the organization. We drew up a hypothetical list of processes that an employee will go through, as well as an inventory of the data elements necessary for the processing of every step in the employee life cycle.
This time, I will share my proposed project management approach towards data privacy compliance, and this proposed project management approach will be applied to the pre-employment stage in the hypothetical employment scenario outlined for this series.
Step 1. Create an Inventory of Processes, Documents, and Policies
The following aspects for each HR process must be mapped out into a matrix:
- HR Function
- Subprocess
- Documentary requirements for each subprocess
- Originator
- Recipient
- Rationale for the submission
- Data elements contained in the document
- Type of Data
By mapping each HR function’s process in this way, the organization will be able to determine the following:
- Whether or not such documentary requirement is an absolute necessity for the function;
- Whether such documentary requirements require additional safeguards such as waivers or undertakings from an employee;
- Whether or not the policy that necessitates such submission may be adjusted given the new law; and lastly,
- Whether or not the form containing such data elements need to be revised given the new law
The organization, of course, may find some processes, documentary requirements, and policies no longer germane or relevant for the purposes that they wish to achieve, so this would be the most opportune time for a process review.
Further, this would ensure that the organization has complied with the general data privacy principles set forth in Section 11 of the Data Privacy Law. It is highly recommended that the organization keep records of such an exercise, in the event that the Data Privacy Commission requires that employers submit proof of compliance thereof.
Step 2. Assess and refine, if necessary, existing controls in the processes
This is where a robust business controls and information security support organization comes in handy. What must be assessed at this point? Section 20 of the Data Privacy Law requires that organizations employ three levels of protection over data in its custody- organizational, physical, and technical. Organizational measures would entail separation of duties between and among participants in handling PI and SPI; physical measures would refer to access restrictions to areas where PI and SPI are stored; technical measures would refer to data security measures such as encryption and secure messaging for communications with PI and SPI. Each process, each transaction, would need to be traced for specific security measures in place to ensure that each time PI and SPI changes hands in connection with a legitimate transaction, the integrity and security of data is not compromised.
Further, the Data Privacy Law requires that organizations report data security breaches. This means that security measures in place must not only be preventive in nature, but there must also be a detective component. In other words, the processes and security measures should be built in such a way that it is readily apparent to key stakeholders if and when a data breach occurs.
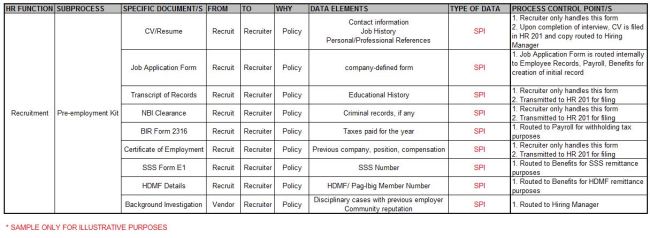
I applied the proposed framework above and came up with this hypothetical example in assessing the Pre-employment stage, specifically the Pre-employment Kit:
I purposely left out an assessment over the security measures over each kind of data to leave the reader with the flexibility to do a separate assessment, or to assess it side-by-side with the process side.
My recommendation would be to have a separate assessment over the security measures once all the data privacy process assessments have been completed.
For the next installment we’ll apply the same methodology to other HR processes to illustrate further that there is a real need for organizations to review HR processes and bring them up to speed with the requirements of the Data Privacy Law.